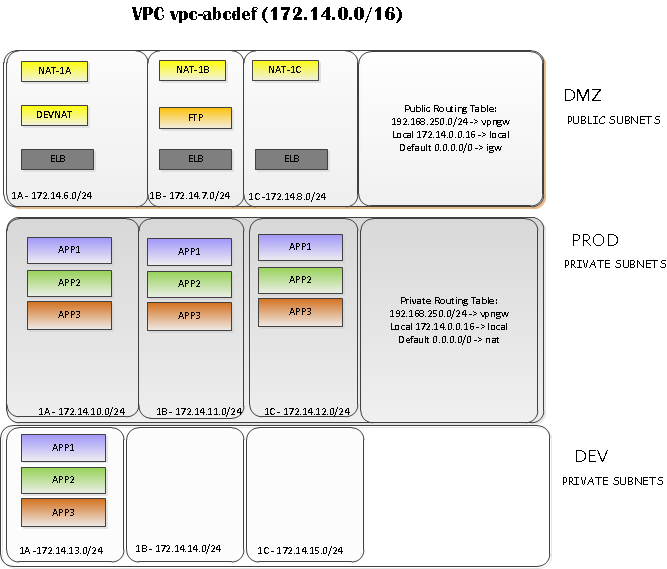
Amazon Virtual Private Cloud (VPC) provides a framework for building virtual datacenters within AWS.
Basic VPC concepts include:
- VPC itself
- Subnets (Private or public)
- Route Tables (Subnet routing behaviour)
- Internet, NAT and VPN Gateways (Routing functionality)
- ACLS (VPC network access controls, similar to router screening)
- Security Groups (Essentially, instance firewall rules)
- ELB (Internal and external load balancing)
VPC
A VPC itself is a container for organizing network resources.
Each VPC object has two major attributes: VPC ID (vpc-12345678) and network (eg: 172.16.0.0/16) . The default netmask for a VPC is a /16 (65536 hosts)
Subnets
A subnet provides virtual network segmentation similar to a VLAN or physical broadcast domain.
Each subnets is assigned a network block (172.16.99.0/24) and a subnet id (eg: subnet-abcd1245) .
There are two flavors of subnet; Public and Private .
Public Subnets
Public subnets are internet routable and may contain resources such as ELBs, EC2 instances, etc. A public subnet is associated with a route table which directs its default route (0.0.0.0) through a pre-defined Internet Gateway device (IGW) .
An EC2 instance defined within a public VPC subnet has no internet connectivity until it has been associated with an EIP. Internet traffic from a public subnet is routed from the source address of each EIP.
Private Subnets
Private subnets are utilized to pass traffic between public subnets, other private subnets, VPN links, etc.
Optionally, a private subnet or subnets can obtain internet access by directing traffic through an EC2 NAT instance with an associated EIP.
Route tables
Route tables are utilized to construct both private and public subnets. They are also used to implement VPN links in coordination with VPC VPN gateways.
Each subnet may be associated with only one route table at any given time.
Load Balancing
Elastic Load Balancing (ELB) may be implemented within VPC. One or more public subnets are associated with each ELB.
Inter-Region failover can be achieved by building applications across subnets which span Availability Zones:
Externally-facing ELBS must be associated with public subnets . Be aware that subnets attached to an ELB must be at minimum a /24 (256 hosts) !